
Quantum Computing vs Classical: Visualizing the Difference
Visualize how quantum computing differs from classical computing. Interactive maze simulator shows superposition, interference, and wave function collapse.
Loading...
Explore our collection of tutorials, guides, and insights to help you master Python and beyond.

Visualize how quantum computing differs from classical computing. Interactive maze simulator shows superposition, interference, and wave function collapse.
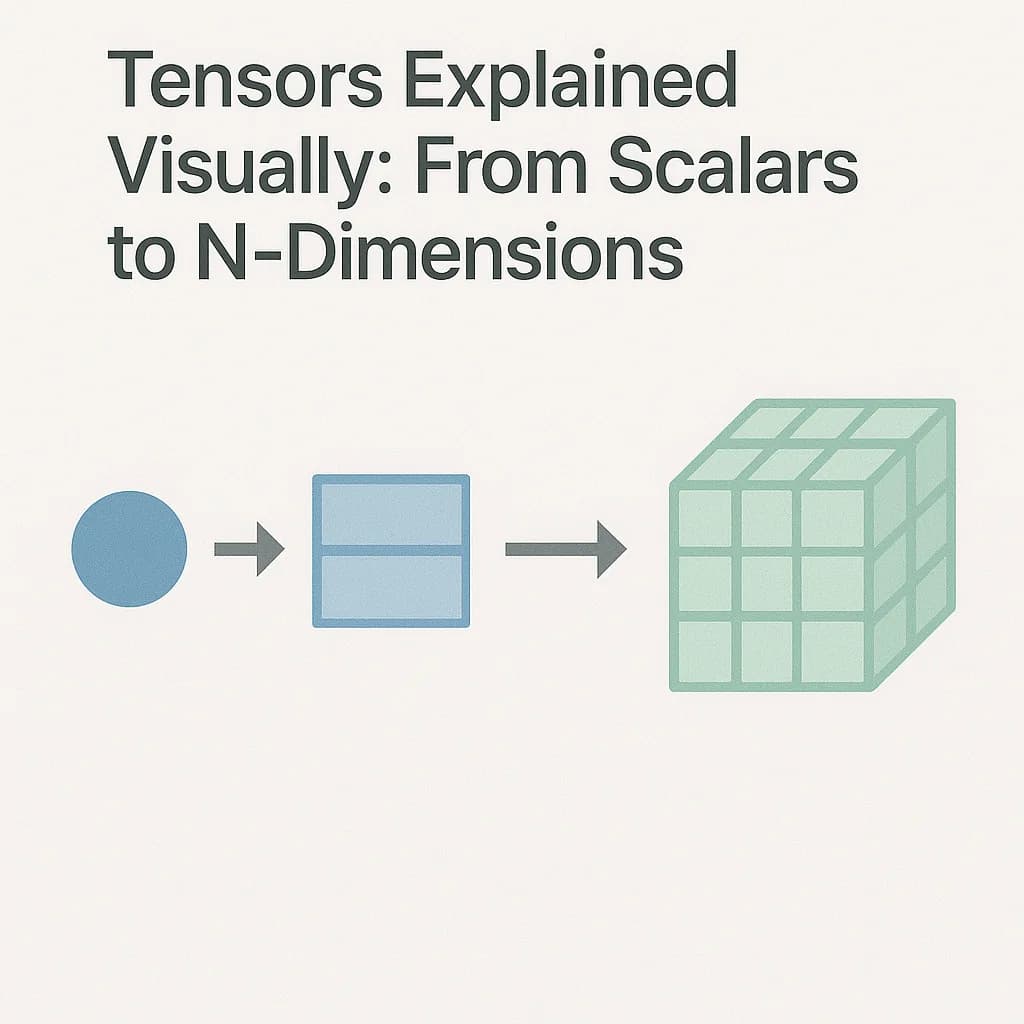
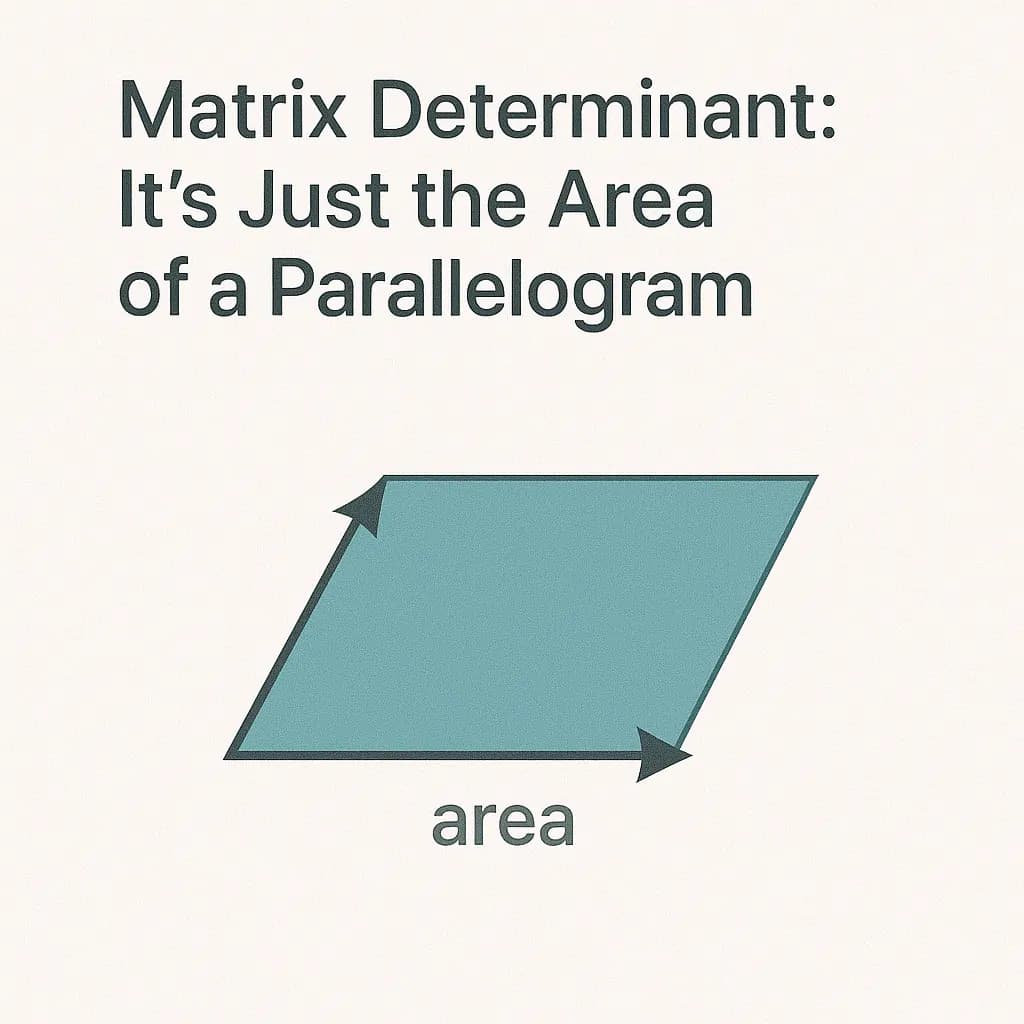
The determinant is just the area of the parallelogram formed by the column vectors. Interactive calculator shows how columns create parallelograms.
Understand eigenvectors through the spinning globe analogy. Interactive calculator to find eigenvectors and eigenvalues of any 2x2 or 3x3 matrix.

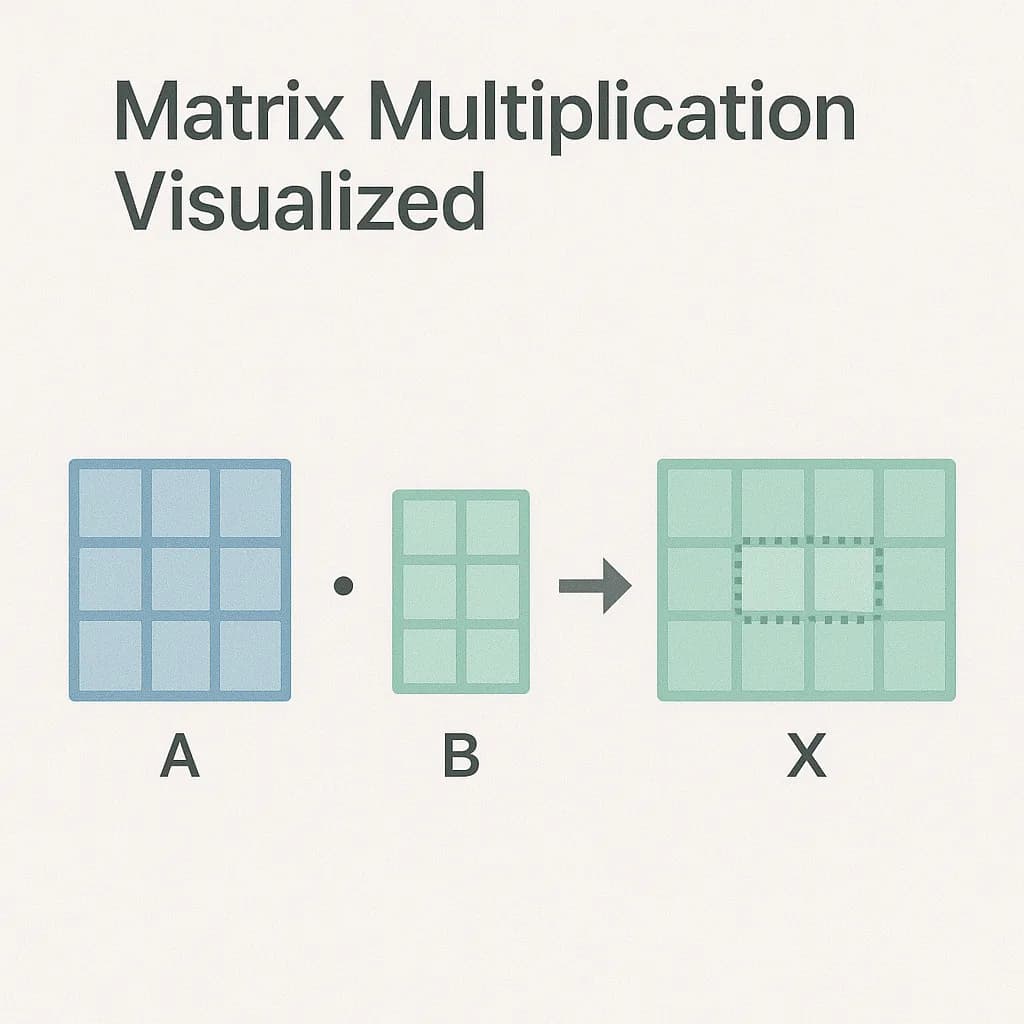
Learn matrix multiplication with an interactive calculator. Change matrix dimensions, enter values, and see step-by-step how each result entry is computed.
Understand tensors visually: scalar vs vector vs matrix vs tensor. Learn NumPy shape intuition with interactive examples and visualizations.

Finally understand Python's self keyword through an interactive puppet theater. Watch the invisible hand connect methods to objects in real-time.
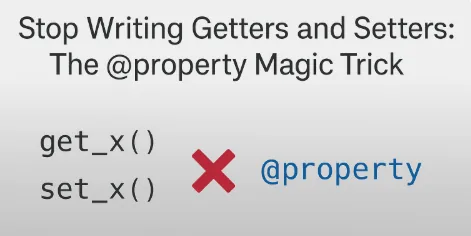
Learn why Python's @property decorator eliminates the need for getters and setters. Interactive vending machine simulator shows encapsulation the Pythonic way.

Master Python dunder methods through an interactive social club simulator. Learn __init__, __str__, __repr__, operator overloading, and protocol-oriented programming.
Learn why composition beats inheritance in Python through an interactive robot workshop. Build modular code like Lego bricks, not glued-together messes.
Visualize how Pandas groupby works with the Split-Apply-Combine pattern. Interactive fruit sorting simulator shows why transform is faster than apply for group operations.

Learn why your Pandas DataFrame is 10x larger than it should be. Interactive cargo ship simulator shows how object vs category dtype and int64 vs int8 waste memory.
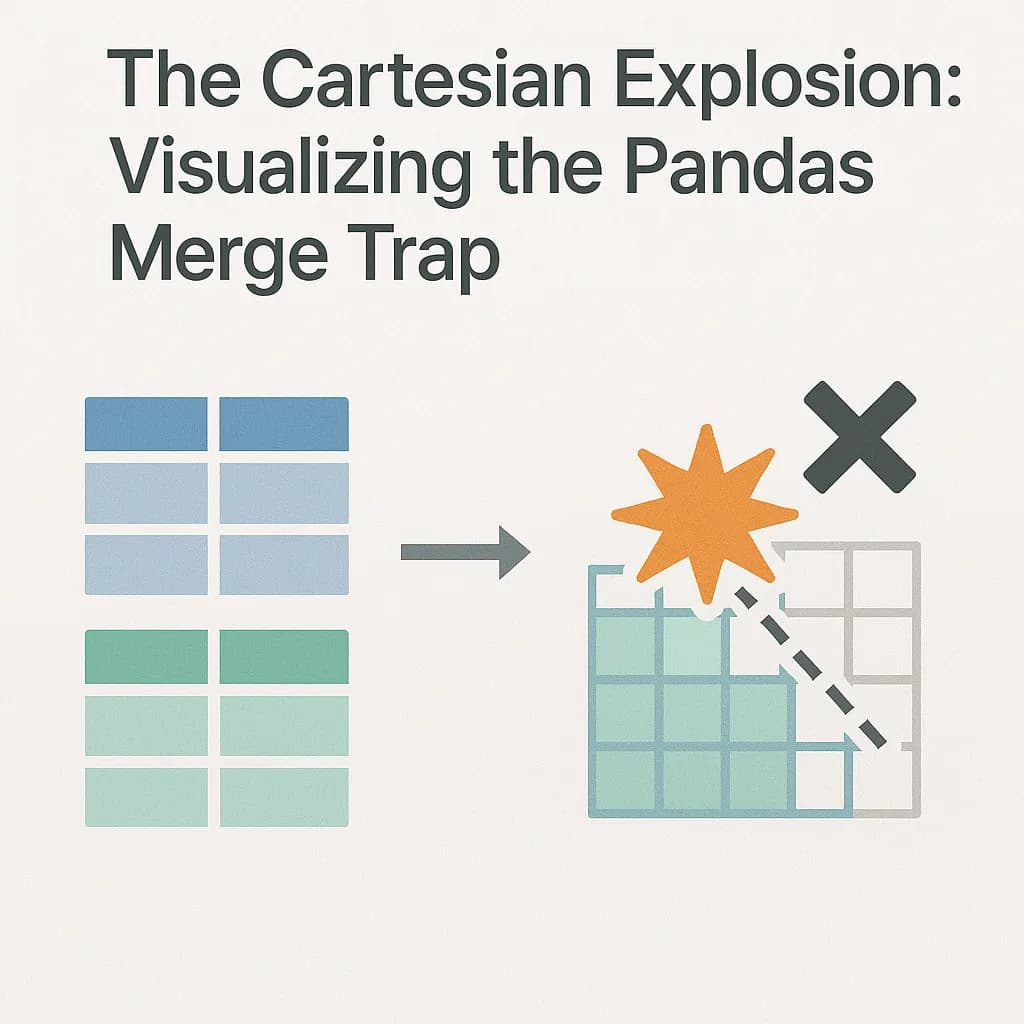
Visualize how Pandas merge creates duplicate rows with many-to-many joins. Interactive dating app simulator shows the Cartesian product explosion that crashes servers.
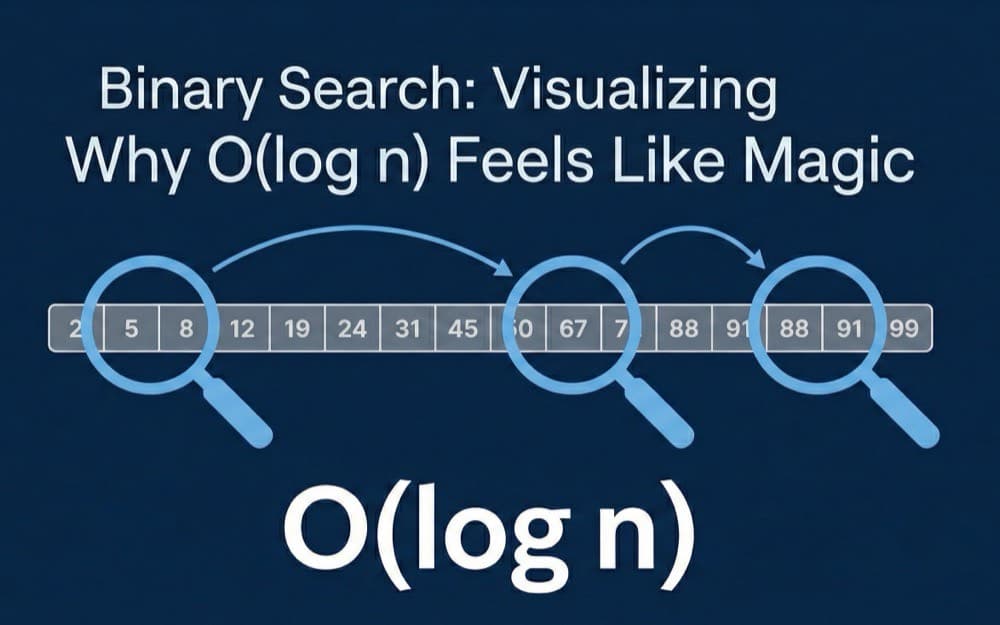
Visualize why O(log n) feels like magic. Watch binary search rip through a phonebook while linear search flips page by page.
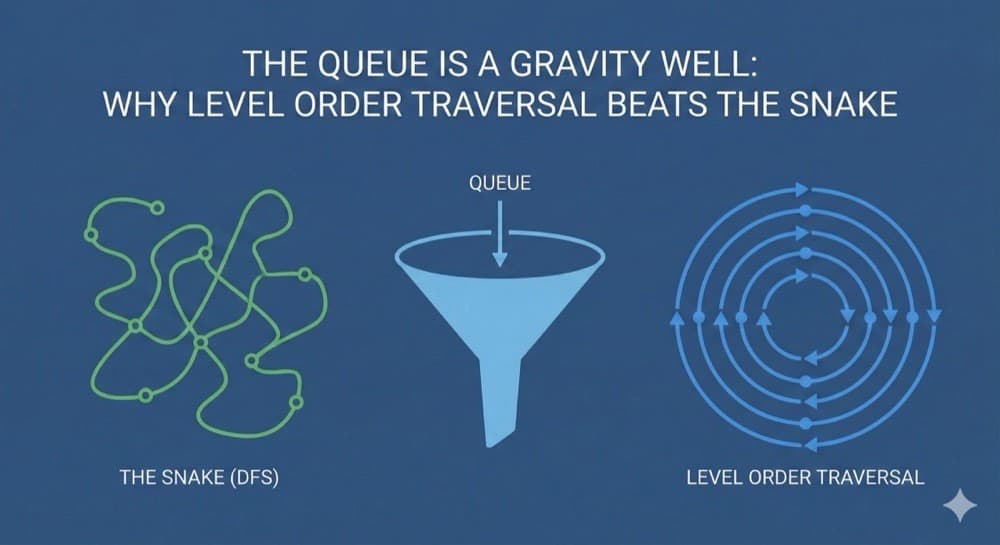
Visualize Level Order Traversal through physics. Watch BFS spread like a sound wave while DFS dives like a snake.

Visualize why naive recursion explodes exponentially. Watch memoization turn chaos into order with an interactive Fibonacci simulator.
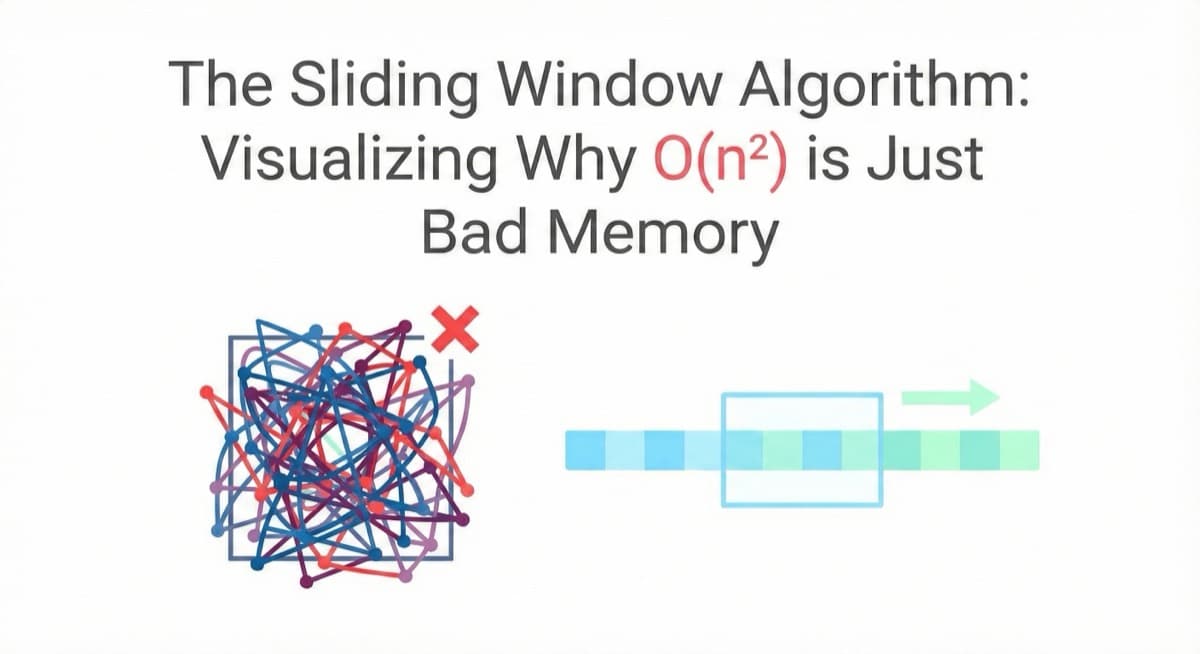
Visualize why O(n²) is inefficient through a heat map simulator. Watch brute force burn CPU cycles while sliding window glides smoothly.
Visualize backtracking through an interactive lock picker simulator. Watch how state reversibility saves memory while brute force creates infinite universes.
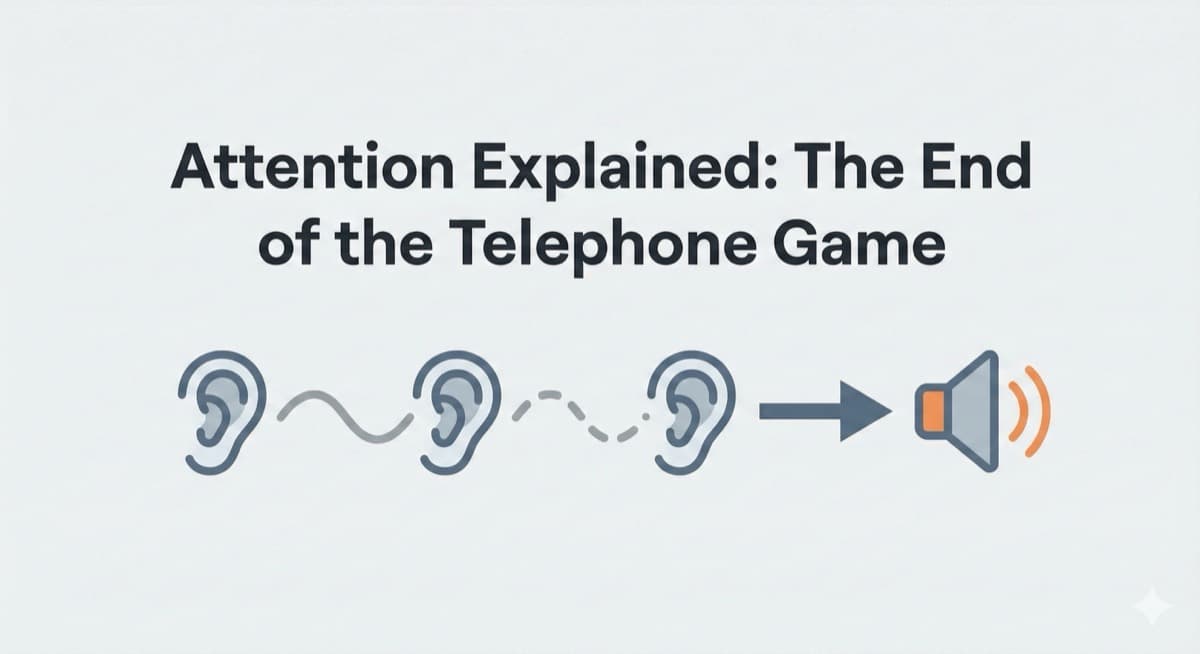
Visualize why RNNs forget and Transformers remember. Watch attention beams bypass the vanishing gradient problem in real-time.
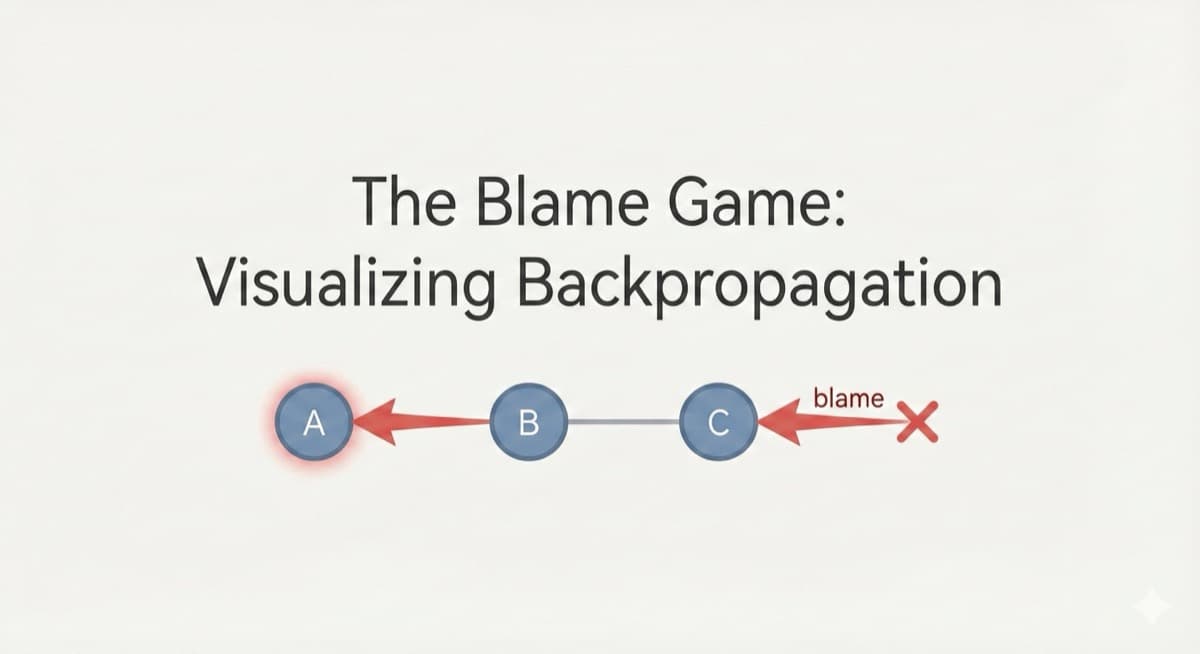
Finally understand backpropagation through an interactive blame game simulator. Wiggle weights and watch error change in real-time.

See why dense neural networks fail at images. Watch 10,000 connections explode into spaghetti while a 9-parameter CNN filter wins.
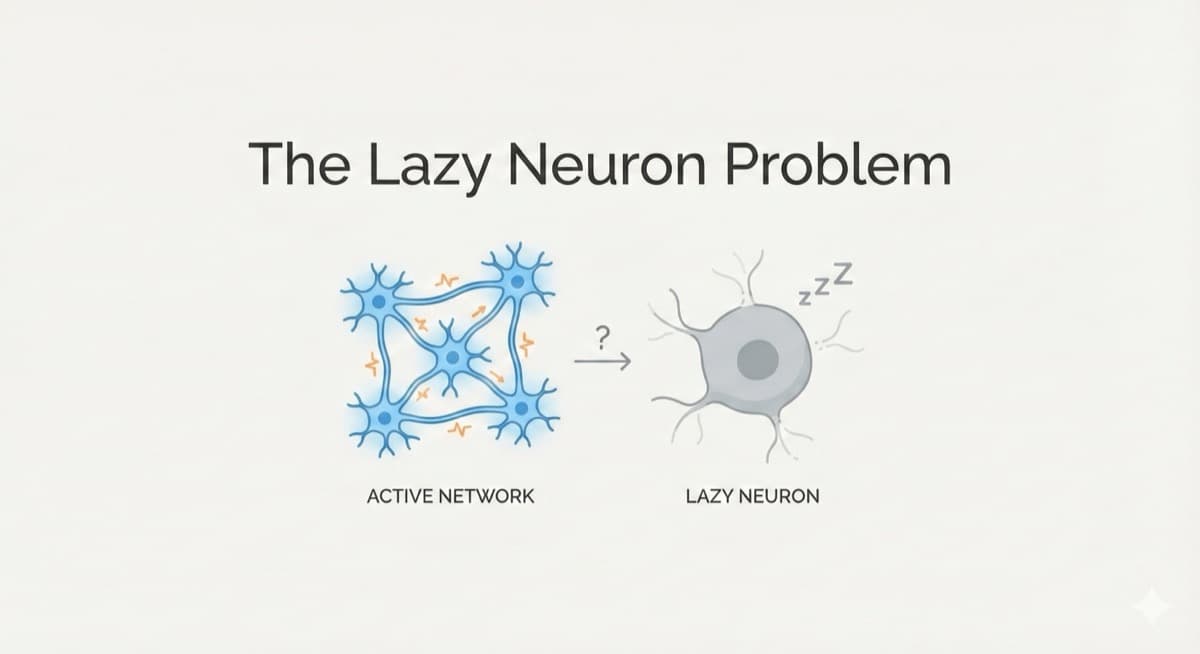
Visualize why randomly killing neurons makes neural networks smarter. Interactive simulator shows how dropout prevents overfitting.
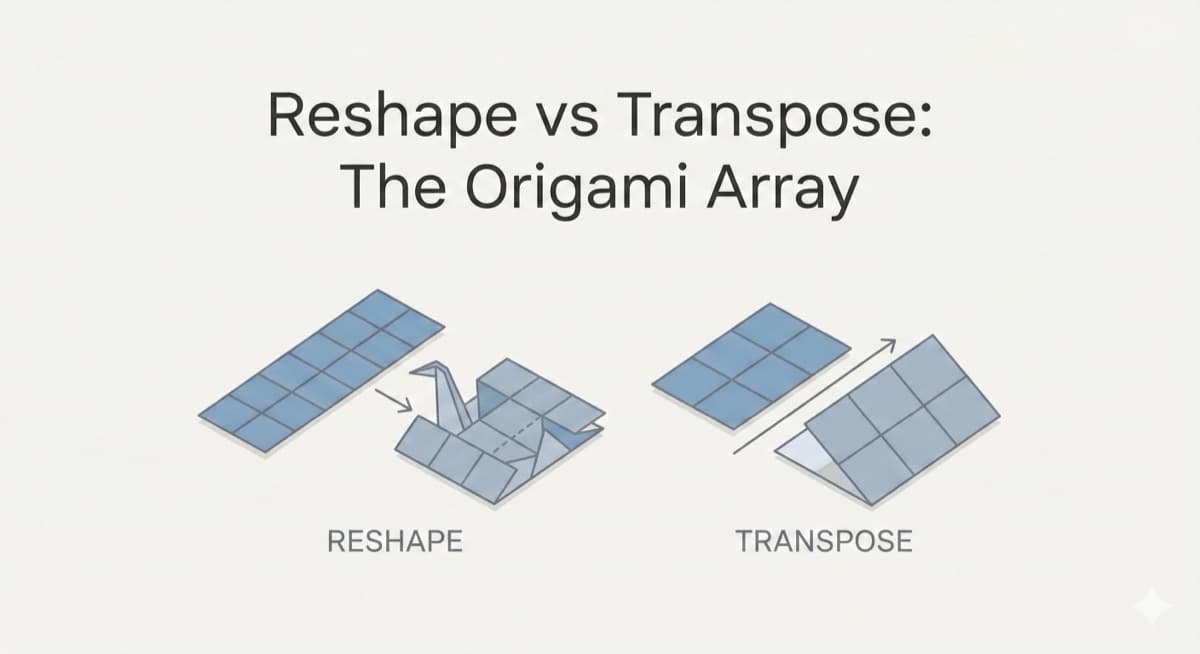
Finally understand the difference between NumPy reshape and transpose. Interactive ribbon simulator shows why reshape(-1) works but can't rotate images.
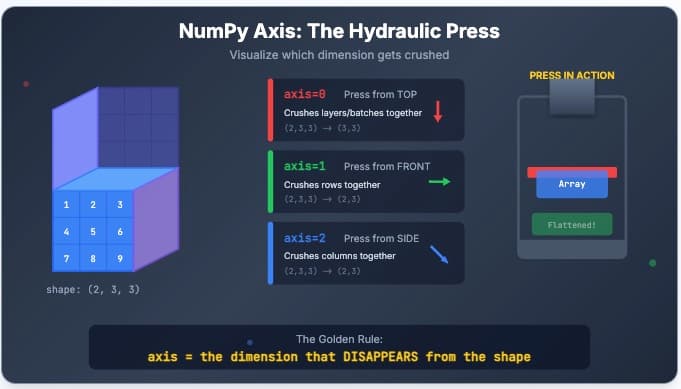
Finally understand NumPy axis with an interactive hydraulic press simulator. Watch axis=0, axis=1, and axis=2 crush a 3D array in real-time.
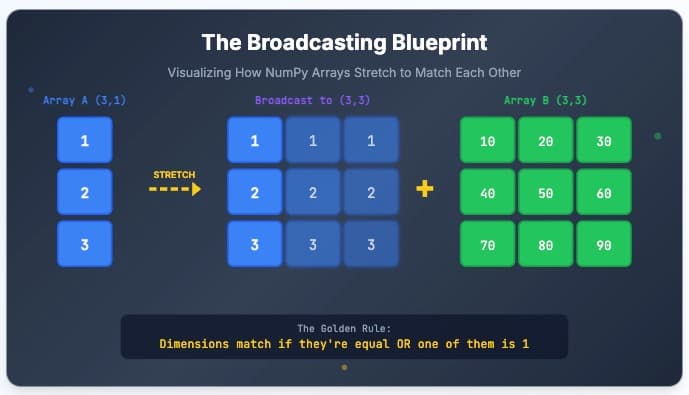
Finally understand NumPy broadcasting through an interactive shape-matching simulator. See exactly why 'operands could not be broadcast together' happens.
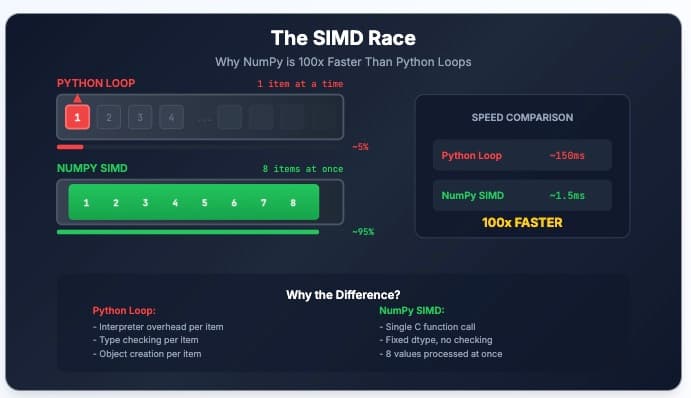
Visualize why NumPy is 100x faster than Python loops. Watch a robot arm vs bulldozer race to finally understand SIMD and vectorization.
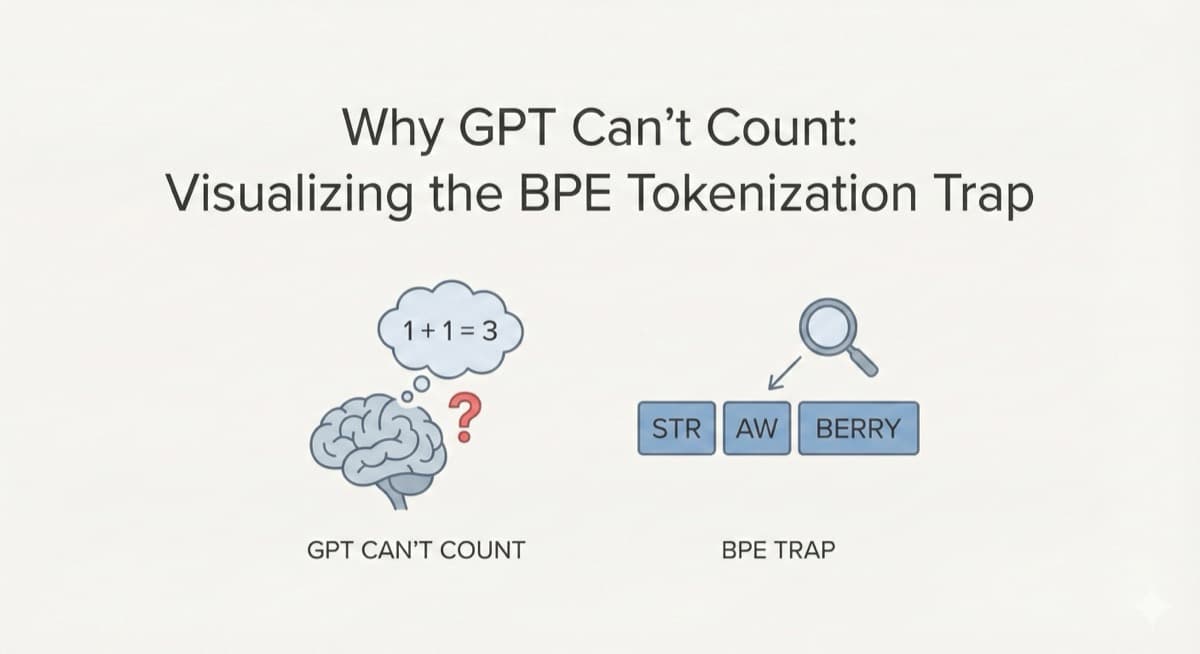
Interactive visualization of Byte Pair Encoding (BPE) tokenization. Discover why GPT thinks 9.11 > 9.9 and watch the tokenizer chop your text in real-time.

Interactive visualization of RNN vs Transformer architecture. See why RNNs forget and how Transformers solve the vanishing gradient problem.

Interactive visualization of self-attention in transformers. See how LLMs decide which words matter using Query, Key, Value.

Interactive visualization of Word2Vec and word embeddings. See why good and great were strangers in one-hot encoding but neighbors in vector space.
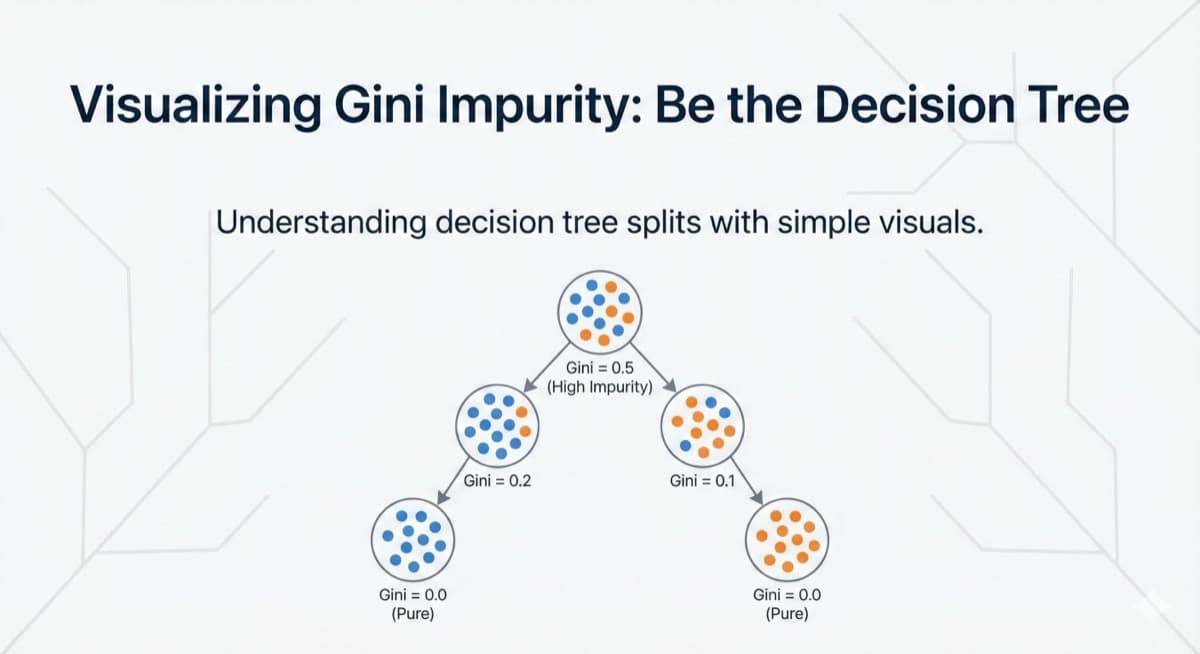
Interactive Gini Impurity calculator. Drag points between classes and watch the split quality update in real-time. Finally understand why decision trees split where they do.

Interactive SVM kernel trick visualization. Draw non-linear data and watch it get lifted into higher dimensions where a simple line can separate it.

See why K-Means clustering fails with bad initialization. Interactive simulator lets you place centroids and watch the algorithm get trapped in local optima.
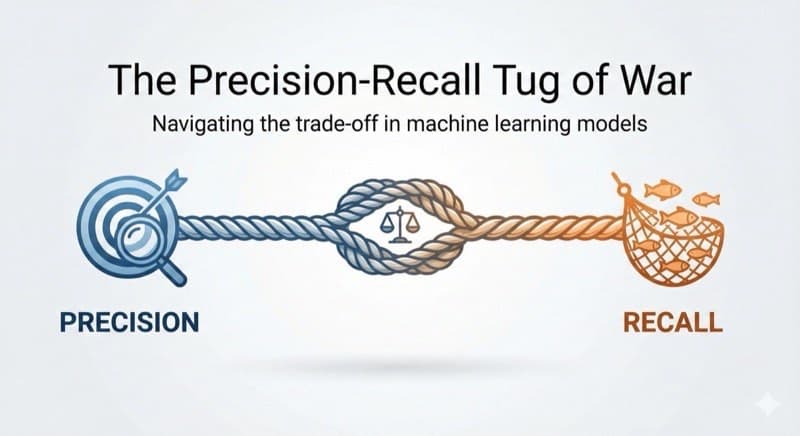
Interactive precision vs recall visualizer. Drag the threshold slider and watch the confusion matrix update in real-time. Finally understand the F1 score tradeoff.